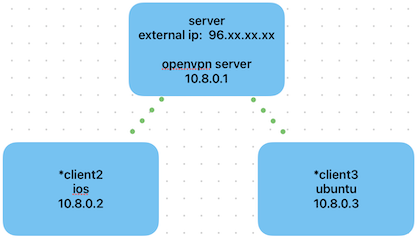
Server with static IP address 96.XX.XX.XX
OpenVPN network: 10.8.0.0/24
OpenVPN server: 10.8.0.1
OpenVPN client2: 10.8.0.2 (ios)
OpenVPN client3: 10.8.0.3 (ubuntu)
etc.
All clients connect to the OpenVPN server and access the internet through the VDS.
However, client2 should uses client3 as default gateway.
Client2's packets targeted to any IP on the internet except for the OpenVPN server will first go to the server and then to client3 and then to the internet from client3.
Can anyone give me a hint on how to do this correctly?
Server config
Code: Select all
port 1194
proto tcp
explicit-exit-notify 0
dev tun
ca ca.crt
cert server.crt
key server.key
dh dh.pem
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist /etc/openvpn/ipp.txt
client-config-dir /etc/openvpn/ccd
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 208.67.222.222"
push "dhcp-option DNS 208.67.220.220"
#client-to-client
keepalive 10 120
tls-crypt ta.key
cipher AES-256-GCM
auth SHA256
user nobody
group nobody
persist-key
persist-tun
status /var/log/openvpn/openvpn-status.log
log /var/log/openvpn/openvpn.log
verb 3
Code: Select all
ifconfig-push 10.8.0.2 255.255.255.0Code: Select all
ifconfig-push 10.8.0.3 255.255.255.0
iroute 0.0.0.0 0.0.0.0Code: Select all
client3,10.8.0.3,I added the rules to ufw /etc/ufw/before.rules
Code: Select all
# START OPENVPN RULES
*nat
:POSTROUTING ACCEPT [0:0]
-A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
-A PREROUTING -i tun0 -s 10.8.0.2 -j DNAT --to-destination 10.8.0.3
COMMIT
# END OPENVPN RULES
echo "200 vpnclient" >> /etc/iproute2/rt_tables
ip route add 10.8.0.0/24 dev tun0 src 10.8.0.1 table vpnclient
ip route add default via 10.8.0.3 dev tun0 table vpnclient
ip rule add from 10.8.0.2 table vpnclient
ip rule add to 10.8.0.2 table vpnclient
ip route flush cache
On client2 (ios) openvpn config
Code: Select all
client
dev tun
proto tcp
remote 96.XX.XX.XX
port 1194
tls-client
remote-cert-tls server
cipher AES-256-GCM
auth SHA256
dhcp-option DNS 208.67.222.222
dhcp-option DNS 208.67.220.220
resolv-retry infinite
nobind
persist-tun
persist-key
verb 3
<ca></ca>
<cert></cert>
<key></key>
<tls-crypt></tls-crypt>Code: Select all
client
dev tun
proto tcp
remote 96.XX.XX.XX
port 1194
tls-client
remote-cert-tls server
cipher AES-256-GCM
auth SHA256
pull-filter ignore redirect-gateway
dhcp-option DNS 208.67.222.222
dhcp-option DNS 208.67.220.220
resolv-retry infinite
nobind
persist-tun
persist-key
verb 3
status /var/log/openvpn/openvpn-status.log
log /var/log/openvpn/openvpn.log
<ca></ca>
<cert></cert>
<key></key>
<tls-crypt></tls-crypt>Code: Select all
net.ipv4.ip_forward=1Code: Select all
# START OPENVPN RULES
*nat
:POSTROUTING ACCEPT [0:0]
-A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
COMMIT
# END OPENVPN RULESThe server can reach the clients (verified with ping)
But nothing opens for example google.com on client2, although 172.217.22.14 is pinged in the console,
I have no idea where I made a mistake.
Thank you in advance,
Vito
