I configured my own VPN Server and can sucessfully connect to it:
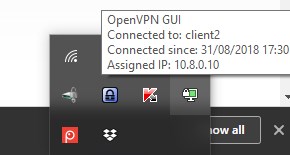
Client LOG:
Code: Select all
Fri Aug 31 17:30:44 2018 NOTE: --user option is not implemented on Windows
Fri Aug 31 17:30:44 2018 NOTE: --group option is not implemented on Windows
Fri Aug 31 17:30:44 2018 OpenVPN 2.4.6 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 26 2018
Fri Aug 31 17:30:44 2018 Windows version 6.2 (Windows 8 or greater) 64bit
Fri Aug 31 17:30:44 2018 library versions: OpenSSL 1.1.0h 27 Mar 2018, LZO 2.10
Fri Aug 31 17:30:44 2018 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Fri Aug 31 17:30:44 2018 Need hold release from management interface, waiting...
Fri Aug 31 17:30:44 2018 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
Fri Aug 31 17:30:44 2018 MANAGEMENT: CMD 'state on'
Fri Aug 31 17:30:44 2018 MANAGEMENT: CMD 'log all on'
Fri Aug 31 17:30:44 2018 MANAGEMENT: CMD 'echo all on'
Fri Aug 31 17:30:44 2018 MANAGEMENT: CMD 'bytecount 5'
Fri Aug 31 17:30:44 2018 MANAGEMENT: CMD 'hold off'
Fri Aug 31 17:30:44 2018 MANAGEMENT: CMD 'hold release'
Fri Aug 31 17:30:44 2018 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Aug 31 17:30:44 2018 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Aug 31 17:30:44 2018 TCP/UDP: Preserving recently used remote address: [AF_INET]35.185.54.105:1194
Fri Aug 31 17:30:44 2018 Socket Buffers: R=[65536->65536] S=[65536->65536]
Fri Aug 31 17:30:44 2018 UDP link local: (not bound)
Fri Aug 31 17:30:44 2018 UDP link remote: [AF_INET]35.185.54.105:1194
Fri Aug 31 17:30:44 2018 MANAGEMENT: >STATE:1535729444,WAIT,,,,,,
Fri Aug 31 17:30:44 2018 MANAGEMENT: >STATE:1535729444,AUTH,,,,,,
Fri Aug 31 17:30:44 2018 TLS: Initial packet from [AF_INET]35.185.54.105:1194, sid=67916b4c e101bc5c
Fri Aug 31 17:30:45 2018 VERIFY OK: depth=1, C=US, ST=CA, L=Berkeley, O=TheImperium, OU=StormTroopers, CN=TheImperium CA, name=gh1server, emailAddress=nomail@here.com
Fri Aug 31 17:30:45 2018 VERIFY KU OK
Fri Aug 31 17:30:45 2018 Validating certificate extended key usage
Fri Aug 31 17:30:45 2018 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Fri Aug 31 17:30:45 2018 VERIFY EKU OK
Fri Aug 31 17:30:45 2018 VERIFY OK: depth=0, C=US, ST=CA, L=Berkeley, O=TheImperium, OU=StormTroopers, CN=server, name=gh1server, emailAddress=nomail@here.com
Fri Aug 31 17:30:45 2018 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Fri Aug 31 17:30:45 2018 [server] Peer Connection Initiated with [AF_INET]35.185.54.105:1194
Fri Aug 31 17:30:46 2018 MANAGEMENT: >STATE:1535729446,GET_CONFIG,,,,,,
Fri Aug 31 17:30:46 2018 SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Fri Aug 31 17:30:46 2018 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,route 10.8.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.10 10.8.0.9,peer-id 1,cipher AES-256-GCM'
Fri Aug 31 17:30:46 2018 OPTIONS IMPORT: timers and/or timeouts modified
Fri Aug 31 17:30:46 2018 OPTIONS IMPORT: --ifconfig/up options modified
Fri Aug 31 17:30:46 2018 OPTIONS IMPORT: route options modified
Fri Aug 31 17:30:46 2018 OPTIONS IMPORT: peer-id set
Fri Aug 31 17:30:46 2018 OPTIONS IMPORT: adjusting link_mtu to 1624
Fri Aug 31 17:30:46 2018 OPTIONS IMPORT: data channel crypto options modified
Fri Aug 31 17:30:46 2018 Data Channel: using negotiated cipher 'AES-256-GCM'
Fri Aug 31 17:30:46 2018 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Fri Aug 31 17:30:46 2018 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Fri Aug 31 17:30:46 2018 interactive service msg_channel=628
Fri Aug 31 17:30:46 2018 ROUTE_GATEWAY 192.168.8.1/255.255.255.0 I=21 HWADDR=00:1f:1f:46:83:22
Fri Aug 31 17:30:46 2018 open_tun
Fri Aug 31 17:30:46 2018 TAP-WIN32 device [Ethernet 5] opened: \\.\Global\{AB0CE83A-E33C-4EF2-9A71-4F85B5597C56}.tap
Fri Aug 31 17:30:46 2018 TAP-Windows Driver Version 9.21
Fri Aug 31 17:30:46 2018 Notified TAP-Windows driver to set a DHCP IP/netmask of 10.8.0.10/255.255.255.252 on interface {AB0CE83A-E33C-4EF2-9A71-4F85B5597C56} [DHCP-serv: 10.8.0.9, lease-time: 31536000]
Fri Aug 31 17:30:46 2018 Successful ARP Flush on interface [17] {AB0CE83A-E33C-4EF2-9A71-4F85B5597C56}
Fri Aug 31 17:30:46 2018 do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Fri Aug 31 17:30:46 2018 MANAGEMENT: >STATE:1535729446,ASSIGN_IP,,10.8.0.10,,,,
Fri Aug 31 17:30:51 2018 TEST ROUTES: 2/2 succeeded len=1 ret=1 a=0 u/d=up
Fri Aug 31 17:30:51 2018 C:\WINDOWS\system32\route.exe ADD 35.185.54.105 MASK 255.255.255.255 192.168.8.1
Fri Aug 31 17:30:51 2018 Route addition via service succeeded
Fri Aug 31 17:30:51 2018 C:\WINDOWS\system32\route.exe ADD 0.0.0.0 MASK 128.0.0.0 10.8.0.9
Fri Aug 31 17:30:51 2018 Route addition via service succeeded
Fri Aug 31 17:30:51 2018 C:\WINDOWS\system32\route.exe ADD 128.0.0.0 MASK 128.0.0.0 10.8.0.9
Fri Aug 31 17:30:51 2018 Route addition via service succeeded
Fri Aug 31 17:30:51 2018 MANAGEMENT: >STATE:1535729451,ADD_ROUTES,,,,,,
Fri Aug 31 17:30:51 2018 C:\WINDOWS\system32\route.exe ADD 10.8.0.1 MASK 255.255.255.255 10.8.0.9
Fri Aug 31 17:30:51 2018 Route addition via service succeeded
Fri Aug 31 17:30:51 2018 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Fri Aug 31 17:30:51 2018 Initialization Sequence Completed
Fri Aug 31 17:30:51 2018 MANAGEMENT: >STATE:1535729451,CONNECTED,SUCCESS,10.8.0.10,35.185.54.105,1194,,
Fri Aug 31 17:32:38 2018 AEAD Decrypt error: bad packet ID (may be a replay): [ #6427 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Fri Aug 31 17:32:38 2018 AEAD Decrypt error: bad packet ID (may be a replay): [ #6428 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Code: Select all
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 TLS: Initial packet from [AF_INET]109.40.2.25:3011, sid=3ddf0f93 b4069bab
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 VERIFY OK: depth=1, C=US, ST=CA, L=Berkeley, O=TheImperium, OU=StormTroopers, CN=TheImperium CA, name=gh1server, emailAddress=nomail@here.com
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 VERIFY OK: depth=0, C=US, ST=CA, L=Berkeley, O=TheImperium, OU=StormTroopers, CN=client2, name=gh1server, emailAddress=nomail@here.com
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_VER=2.4.6
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_PLAT=win
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_PROTO=2
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_NCP=2
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_LZ4=1
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_LZ4v2=1
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_LZO=1
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_COMP_STUB=1
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_COMP_STUBv2=1
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_TCPNL=1
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 peer info: IV_GUI_VER=OpenVPN_GUI_11
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Fri Aug 31 15:30:43 2018 109.40.2.25:3011 [client2] Peer Connection Initiated with [AF_INET]109.40.2.25:3011
Fri Aug 31 15:30:43 2018 MULTI: new connection by client 'client2' will cause previous active sessions by this client to be dropped. Remember to use the --duplicate-cn option if you want multiple clients using the same certificate or username to concurrently connect.
Fri Aug 31 15:30:43 2018 MULTI_sva: pool returned IPv4=10.8.0.10, IPv6=(Not enabled)
Fri Aug 31 15:30:43 2018 MULTI: Learn: 10.8.0.10 -> client2/109.40.2.25:3011
Fri Aug 31 15:30:43 2018 MULTI: primary virtual IP for client2/109.40.2.25:3011: 10.8.0.10
Fri Aug 31 15:30:44 2018 client2/109.40.2.25:3011 PUSH: Received control message: 'PUSH_REQUEST'
Fri Aug 31 15:30:44 2018 client2/109.40.2.25:3011 SENT CONTROL [client2]: 'PUSH_REPLY,redirect-gateway def1,route 10.8.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.10 10.8.0.9,peer-id 1,cipher AES-256-GCM' (status=1)
Fri Aug 31 15:30:44 2018 client2/109.40.2.25:3011 Data Channel: using negotiated cipher 'AES-256-GCM'
Fri Aug 31 15:30:44 2018 client2/109.40.2.25:3011 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Fri Aug 31 15:30:44 2018 client2/109.40.2.25:3011 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Fri Aug 31 15:55:14 2018 client2/109.40.2.25:3011 [client2] Inactivity timeout (--ping-restart), restarting
Fri Aug 31 15:55:14 2018 client2/109.40.2.25:3011 SIGUSR1[soft,ping-restart] received, client-instance restarting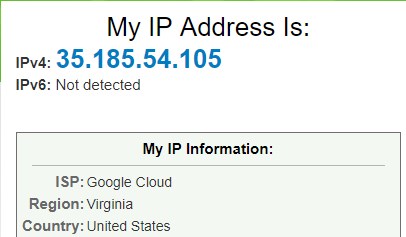
But when I try to connect to a site (for reading scientific papers) which is blocked by my ISP (for copyright reasons) I see their webblock page instead of the desired page. That is surprising because I thought that my traffic is encrypted and cannot be read by my ISP. But it seems that I did not configure it properly but I do not know what to change. The log file says that the connection is encrypted and it seems that my IP also changed?!

My server configuration is as following:
server
#################################################
# Sample OpenVPN 2.0 config file for #
# multi-client server. #
# #
# This file is for the server side #
# of a many-clients <-> one-server #
# OpenVPN configuration. #
# #
# OpenVPN also supports #
# single-machine <-> single-machine #
# configurations (See the Examples page #
# on the web site for more info). #
# #
# This config should work on Windows #
# or Linux/BSD systems. Remember on #
# Windows to quote pathnames and use #
# double backslashes, e.g.: #
# "C:\\Program Files\\OpenVPN\\config\\foo.key" #
# #
# Comments are preceded with '#' or ';' #
#################################################
# Which local IP address should OpenVPN
# listen on? (optional)
;local a.b.c.d
# Which TCP/UDP port should OpenVPN listen on?
# If you want to run multiple OpenVPN instances
# on the same machine, use a different port
# number for each one. You will need to
# open up this port on your firewall.
port 1194
# TCP or UDP server?
;proto tcp
proto udp
# "dev tun" will create a routed IP tunnel,
# "dev tap" will create an ethernet tunnel.
# Use "dev tap0" if you are ethernet bridging
# and have precreated a tap0 virtual interface
# and bridged it with your ethernet interface.
# If you want to control access policies
# over the VPN, you must create firewall
# rules for the the TUN/TAP interface.
# On non-Windows systems, you can give
# an explicit unit number, such as tun0.
# On Windows, use "dev-node" for this.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
;dev tap
dev tun
# Windows needs the TAP-Win32 adapter name
# from the Network Connections panel if you
# have more than one. On XP SP2 or higher,
# you may need to selectively disable the
# Windows firewall for the TAP adapter.
# Non-Windows systems usually don't need this.
;dev-node MyTap
# SSL/TLS root certificate (ca), certificate
# (cert), and private key (key). Each client
# and the server must have their own cert and
# key file. The server and all clients will
# use the same ca file.
#
# See the "easy-rsa" directory for a series
# of scripts for generating RSA certificates
# and private keys. Remember to use
# a unique Common Name for the server
# and each of the client certificates.
#
# Any X509 key management system can be used.
# OpenVPN can also use a PKCS #12 formatted key file
# (see "pkcs12" directive in man page).
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
# Diffie hellman parameters.
# Generate your own with:
# openssl dhparam -out dh2048.pem 2048
dh dh2048.pem
# Network topology
# Should be subnet (addressing via IP)
# unless Windows clients v2.0.9 and lower have to
# be supported (then net30, i.e. a /30 per client)
# Defaults to net30 (not recommended)
;topology subnet
# Configure server mode and supply a VPN subnet
# for OpenVPN to draw client addresses from.
# The server will take 10.8.0.1 for itself,
# the rest will be made available to clients.
# Each client will be able to reach the server
# on 10.8.0.1. Comment this line out if you are
# ethernet bridging. See the man page for more info.
server 10.8.0.0 255.255.255.0
# Maintain a record of client <-> virtual IP address
# associations in this file. If OpenVPN goes down or
# is restarted, reconnecting clients can be assigned
# the same virtual IP address from the pool that was
# previously assigned.
ifconfig-pool-persist ipp.txt
# Configure server mode for ethernet bridging.
# You must first use your OS's bridging capability
# to bridge the TAP interface with the ethernet
# NIC interface. Then you must manually set the
# IP/netmask on the bridge interface, here we
# assume 10.8.0.4/255.255.255.0. Finally we
# must set aside an IP range in this subnet
# (start=10.8.0.50 end=10.8.0.100) to allocate
# to connecting clients. Leave this line commented
# out unless you are ethernet bridging.
;server-bridge 10.8.0.4 255.255.255.0 10.8.0.50 10.8.0.100
# Configure server mode for ethernet bridging
# using a DHCP-proxy, where clients talk
# to the OpenVPN server-side DHCP server
# to receive their IP address allocation
# and DNS server addresses. You must first use
# your OS's bridging capability to bridge the TAP
# interface with the ethernet NIC interface.
# Note: this mode only works on clients (such as
# Windows), where the client-side TAP adapter is
# bound to a DHCP client.
;server-bridge
# Push routes to the client to allow it
# to reach other private subnets behind
# the server. Remember that these
# private subnets will also need
# to know to route the OpenVPN client
# address pool (10.8.0.0/255.255.255.0)
# back to the OpenVPN server.
;push "route 192.168.10.0 255.255.255.0"
;push "route 192.168.20.0 255.255.255.0"
# To assign specific IP addresses to specific
# clients or if a connecting client has a private
# subnet behind it that should also have VPN access,
# use the subdirectory "ccd" for client-specific
# configuration files (see man page for more info).
# EXAMPLE: Suppose the client
# having the certificate common name "Thelonious"
# also has a small subnet behind his connecting
# machine, such as 192.168.40.128/255.255.255.248.
# First, uncomment out these lines:
;client-config-dir ccd
;route 192.168.40.128 255.255.255.248
# Then create a file ccd/Thelonious with this line:
# iroute 192.168.40.128 255.255.255.248
# This will allow Thelonious' private subnet to
# access the VPN. This example will only work
# if you are routing, not bridging, i.e. you are
# using "dev tun" and "server" directives.
# EXAMPLE: Suppose you want to give
# Thelonious a fixed VPN IP address of 10.9.0.1.
# First uncomment out these lines:
;client-config-dir ccd
;route 10.9.0.0 255.255.255.252
# Then add this line to ccd/Thelonious:
# ifconfig-push 10.9.0.1 10.9.0.2
# Suppose that you want to enable different
# firewall access policies for different groups
# of clients. There are two methods:
# (1) Run multiple OpenVPN daemons, one for each
# group, and firewall the TUN/TAP interface
# for each group/daemon appropriately.
# (2) (Advanced) Create a script to dynamically
# modify the firewall in response to access
# from different clients. See man
# page for more info on learn-address script.
;learn-address ./script
# If enabled, this directive will configure
# all clients to redirect their default
# network gateway through the VPN, causing
# all IP traffic such as web browsing and
# and DNS lookups to go through the VPN
# (The OpenVPN server machine may need to NAT
# or bridge the TUN/TAP interface to the internet
# in order for this to work properly).
;push "redirect-gateway def1 bypass-dhcp"
push "redirect-gateway def1"
# Certain Windows-specific network settings
# can be pushed to clients, such as DNS
# or WINS server addresses. CAVEAT:
# http://openvpn.net/faq.html#dhcpcaveats
# The addresses below refer to the public
# DNS servers provided by opendns.com.
;push "dhcp-option DNS 208.67.222.222"
;push "dhcp-option DNS 208.67.220.220"
# Uncomment this directive to allow different
# clients to be able to "see" each other.
# By default, clients will only see the server.
# To force clients to only see the server, you
# will also need to appropriately firewall the
# server's TUN/TAP interface.
;client-to-client
# Uncomment this directive if multiple clients
# might connect with the same certificate/key
# files or common names. This is recommended
# only for testing purposes. For production use,
# each client should have its own certificate/key
# pair.
#
# IF YOU HAVE NOT GENERATED INDIVIDUAL
# CERTIFICATE/KEY PAIRS FOR EACH CLIENT,
# EACH HAVING ITS OWN UNIQUE "COMMON NAME",
# UNCOMMENT THIS LINE OUT.
;duplicate-cn
# The keepalive directive causes ping-like
# messages to be sent back and forth over
# the link so that each side knows when
# the other side has gone down.
# Ping every 10 seconds, assume that remote
# peer is down if no ping received during
# a 120 second time period.
keepalive 10 120
# For extra security beyond that provided
# by SSL/TLS, create an "HMAC firewall"
# to help block DoS attacks and UDP port flooding.
#
# Generate with:
# openvpn --genkey --secret ta.key
#
# The server and each client must have
# a copy of this key.
# The second parameter should be '0'
# on the server and '1' on the clients.
tls-auth ta.key 0 # This file is secret
key-direction 0
# Select a cryptographic cipher.
# This config item must be copied to
# the client config file as well.
# Note that 2.4 client/server will automatically
# negotiate AES-256-GCM in TLS mode.
# See also the ncp-cipher option in the manpage
cipher AES-128-CBC
auth SHA256
# Enable compression on the VPN link and push the
# option to the client (2.4+ only, for earlier
# versions see below)
;compress lz4-v2
;push "compress lz4-v2"
# For compression compatible with older clients use comp-lzo
# If you enable it here, you must also
# enable it in the client config file.
;comp-lzo
# The maximum number of concurrently connected
# clients we want to allow.
;max-clients 100
# It's a good idea to reduce the OpenVPN
# daemon's privileges after initialization.
#
# You can uncomment this out on
# non-Windows systems.
user nobody
group nogroup
# The persist options will try to avoid
# accessing certain resources on restart
# that may no longer be accessible because
# of the privilege downgrade.
persist-key
persist-tun
# Output a short status file showing
# current connections, truncated
# and rewritten every minute.
status openvpn-status.log
# By default, log messages will go to the syslog (or
# on Windows, if running as a service, they will go to
# the "\Program Files\OpenVPN\log" directory).
# Use log or log-append to override this default.
# "log" will truncate the log file on OpenVPN startup,
# while "log-append" will append to it. Use one
# or the other (but not both).
;log openvpn.log
log-append openvpn.log
# Set the appropriate level of log
# file verbosity.
#
# 0 is silent, except for fatal errors
# 4 is reasonable for general usage
# 5 and 6 can help to debug connection problems
# 9 is extremely verbose
verb 3
# Silence repeating messages. At most 20
# sequential messages of the same message
# category will be output to the log.
;mute 20
# Notify the client that when the server restarts so it
# can automatically reconnect.
explicit-exit-notify 1
# Sample OpenVPN 2.0 config file for #
# multi-client server. #
# #
# This file is for the server side #
# of a many-clients <-> one-server #
# OpenVPN configuration. #
# #
# OpenVPN also supports #
# single-machine <-> single-machine #
# configurations (See the Examples page #
# on the web site for more info). #
# #
# This config should work on Windows #
# or Linux/BSD systems. Remember on #
# Windows to quote pathnames and use #
# double backslashes, e.g.: #
# "C:\\Program Files\\OpenVPN\\config\\foo.key" #
# #
# Comments are preceded with '#' or ';' #
#################################################
# Which local IP address should OpenVPN
# listen on? (optional)
;local a.b.c.d
# Which TCP/UDP port should OpenVPN listen on?
# If you want to run multiple OpenVPN instances
# on the same machine, use a different port
# number for each one. You will need to
# open up this port on your firewall.
port 1194
# TCP or UDP server?
;proto tcp
proto udp
# "dev tun" will create a routed IP tunnel,
# "dev tap" will create an ethernet tunnel.
# Use "dev tap0" if you are ethernet bridging
# and have precreated a tap0 virtual interface
# and bridged it with your ethernet interface.
# If you want to control access policies
# over the VPN, you must create firewall
# rules for the the TUN/TAP interface.
# On non-Windows systems, you can give
# an explicit unit number, such as tun0.
# On Windows, use "dev-node" for this.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
;dev tap
dev tun
# Windows needs the TAP-Win32 adapter name
# from the Network Connections panel if you
# have more than one. On XP SP2 or higher,
# you may need to selectively disable the
# Windows firewall for the TAP adapter.
# Non-Windows systems usually don't need this.
;dev-node MyTap
# SSL/TLS root certificate (ca), certificate
# (cert), and private key (key). Each client
# and the server must have their own cert and
# key file. The server and all clients will
# use the same ca file.
#
# See the "easy-rsa" directory for a series
# of scripts for generating RSA certificates
# and private keys. Remember to use
# a unique Common Name for the server
# and each of the client certificates.
#
# Any X509 key management system can be used.
# OpenVPN can also use a PKCS #12 formatted key file
# (see "pkcs12" directive in man page).
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
# Diffie hellman parameters.
# Generate your own with:
# openssl dhparam -out dh2048.pem 2048
dh dh2048.pem
# Network topology
# Should be subnet (addressing via IP)
# unless Windows clients v2.0.9 and lower have to
# be supported (then net30, i.e. a /30 per client)
# Defaults to net30 (not recommended)
;topology subnet
# Configure server mode and supply a VPN subnet
# for OpenVPN to draw client addresses from.
# The server will take 10.8.0.1 for itself,
# the rest will be made available to clients.
# Each client will be able to reach the server
# on 10.8.0.1. Comment this line out if you are
# ethernet bridging. See the man page for more info.
server 10.8.0.0 255.255.255.0
# Maintain a record of client <-> virtual IP address
# associations in this file. If OpenVPN goes down or
# is restarted, reconnecting clients can be assigned
# the same virtual IP address from the pool that was
# previously assigned.
ifconfig-pool-persist ipp.txt
# Configure server mode for ethernet bridging.
# You must first use your OS's bridging capability
# to bridge the TAP interface with the ethernet
# NIC interface. Then you must manually set the
# IP/netmask on the bridge interface, here we
# assume 10.8.0.4/255.255.255.0. Finally we
# must set aside an IP range in this subnet
# (start=10.8.0.50 end=10.8.0.100) to allocate
# to connecting clients. Leave this line commented
# out unless you are ethernet bridging.
;server-bridge 10.8.0.4 255.255.255.0 10.8.0.50 10.8.0.100
# Configure server mode for ethernet bridging
# using a DHCP-proxy, where clients talk
# to the OpenVPN server-side DHCP server
# to receive their IP address allocation
# and DNS server addresses. You must first use
# your OS's bridging capability to bridge the TAP
# interface with the ethernet NIC interface.
# Note: this mode only works on clients (such as
# Windows), where the client-side TAP adapter is
# bound to a DHCP client.
;server-bridge
# Push routes to the client to allow it
# to reach other private subnets behind
# the server. Remember that these
# private subnets will also need
# to know to route the OpenVPN client
# address pool (10.8.0.0/255.255.255.0)
# back to the OpenVPN server.
;push "route 192.168.10.0 255.255.255.0"
;push "route 192.168.20.0 255.255.255.0"
# To assign specific IP addresses to specific
# clients or if a connecting client has a private
# subnet behind it that should also have VPN access,
# use the subdirectory "ccd" for client-specific
# configuration files (see man page for more info).
# EXAMPLE: Suppose the client
# having the certificate common name "Thelonious"
# also has a small subnet behind his connecting
# machine, such as 192.168.40.128/255.255.255.248.
# First, uncomment out these lines:
;client-config-dir ccd
;route 192.168.40.128 255.255.255.248
# Then create a file ccd/Thelonious with this line:
# iroute 192.168.40.128 255.255.255.248
# This will allow Thelonious' private subnet to
# access the VPN. This example will only work
# if you are routing, not bridging, i.e. you are
# using "dev tun" and "server" directives.
# EXAMPLE: Suppose you want to give
# Thelonious a fixed VPN IP address of 10.9.0.1.
# First uncomment out these lines:
;client-config-dir ccd
;route 10.9.0.0 255.255.255.252
# Then add this line to ccd/Thelonious:
# ifconfig-push 10.9.0.1 10.9.0.2
# Suppose that you want to enable different
# firewall access policies for different groups
# of clients. There are two methods:
# (1) Run multiple OpenVPN daemons, one for each
# group, and firewall the TUN/TAP interface
# for each group/daemon appropriately.
# (2) (Advanced) Create a script to dynamically
# modify the firewall in response to access
# from different clients. See man
# page for more info on learn-address script.
;learn-address ./script
# If enabled, this directive will configure
# all clients to redirect their default
# network gateway through the VPN, causing
# all IP traffic such as web browsing and
# and DNS lookups to go through the VPN
# (The OpenVPN server machine may need to NAT
# or bridge the TUN/TAP interface to the internet
# in order for this to work properly).
;push "redirect-gateway def1 bypass-dhcp"
push "redirect-gateway def1"
# Certain Windows-specific network settings
# can be pushed to clients, such as DNS
# or WINS server addresses. CAVEAT:
# http://openvpn.net/faq.html#dhcpcaveats
# The addresses below refer to the public
# DNS servers provided by opendns.com.
;push "dhcp-option DNS 208.67.222.222"
;push "dhcp-option DNS 208.67.220.220"
# Uncomment this directive to allow different
# clients to be able to "see" each other.
# By default, clients will only see the server.
# To force clients to only see the server, you
# will also need to appropriately firewall the
# server's TUN/TAP interface.
;client-to-client
# Uncomment this directive if multiple clients
# might connect with the same certificate/key
# files or common names. This is recommended
# only for testing purposes. For production use,
# each client should have its own certificate/key
# pair.
#
# IF YOU HAVE NOT GENERATED INDIVIDUAL
# CERTIFICATE/KEY PAIRS FOR EACH CLIENT,
# EACH HAVING ITS OWN UNIQUE "COMMON NAME",
# UNCOMMENT THIS LINE OUT.
;duplicate-cn
# The keepalive directive causes ping-like
# messages to be sent back and forth over
# the link so that each side knows when
# the other side has gone down.
# Ping every 10 seconds, assume that remote
# peer is down if no ping received during
# a 120 second time period.
keepalive 10 120
# For extra security beyond that provided
# by SSL/TLS, create an "HMAC firewall"
# to help block DoS attacks and UDP port flooding.
#
# Generate with:
# openvpn --genkey --secret ta.key
#
# The server and each client must have
# a copy of this key.
# The second parameter should be '0'
# on the server and '1' on the clients.
tls-auth ta.key 0 # This file is secret
key-direction 0
# Select a cryptographic cipher.
# This config item must be copied to
# the client config file as well.
# Note that 2.4 client/server will automatically
# negotiate AES-256-GCM in TLS mode.
# See also the ncp-cipher option in the manpage
cipher AES-128-CBC
auth SHA256
# Enable compression on the VPN link and push the
# option to the client (2.4+ only, for earlier
# versions see below)
;compress lz4-v2
;push "compress lz4-v2"
# For compression compatible with older clients use comp-lzo
# If you enable it here, you must also
# enable it in the client config file.
;comp-lzo
# The maximum number of concurrently connected
# clients we want to allow.
;max-clients 100
# It's a good idea to reduce the OpenVPN
# daemon's privileges after initialization.
#
# You can uncomment this out on
# non-Windows systems.
user nobody
group nogroup
# The persist options will try to avoid
# accessing certain resources on restart
# that may no longer be accessible because
# of the privilege downgrade.
persist-key
persist-tun
# Output a short status file showing
# current connections, truncated
# and rewritten every minute.
status openvpn-status.log
# By default, log messages will go to the syslog (or
# on Windows, if running as a service, they will go to
# the "\Program Files\OpenVPN\log" directory).
# Use log or log-append to override this default.
# "log" will truncate the log file on OpenVPN startup,
# while "log-append" will append to it. Use one
# or the other (but not both).
;log openvpn.log
log-append openvpn.log
# Set the appropriate level of log
# file verbosity.
#
# 0 is silent, except for fatal errors
# 4 is reasonable for general usage
# 5 and 6 can help to debug connection problems
# 9 is extremely verbose
verb 3
# Silence repeating messages. At most 20
# sequential messages of the same message
# category will be output to the log.
;mute 20
# Notify the client that when the server restarts so it
# can automatically reconnect.
explicit-exit-notify 1
And my client configuration as following:
client
##############################################
# Sample client-side OpenVPN 2.0 config file #
# for connecting to multi-client server. #
# #
# This configuration can be used by multiple #
# clients, however each client should have #
# its own cert and key files. #
# #
# On Windows, you might want to rename this #
# file so it has a .ovpn extension #
##############################################
# Specify that we are a client and that we
# will be pulling certain config file directives
# from the server.
client
# Use the same setting as you are using on
# the server.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
;dev tap
dev tun
# Windows needs the TAP-Win32 adapter name
# from the Network Connections panel
# if you have more than one. On XP SP2,
# you may need to disable the firewall
# for the TAP adapter.
;dev-node MyTap
# Are we connecting to a TCP or
# UDP server? Use the same setting as
# on the server.
;proto tcp
proto udp
# The hostname/IP and port of the server.
# You can have multiple remote entries
# to load balance between the servers.
remote 35.185.54.105
;remote my-server-2 1194
# Choose a random host from the remote
# list for load-balancing. Otherwise
# try hosts in the order specified.
;remote-random
# Keep trying indefinitely to resolve the
# host name of the OpenVPN server. Very useful
# on machines which are not permanently connected
# to the internet such as laptops.
resolv-retry infinite
# Most clients don't need to bind to
# a specific local port number.
nobind
# Downgrade privileges after initialization (non-Windows only)
user nobody
group nogroup
# Try to preserve some state across restarts.
persist-key
persist-tun
# If you are connecting through an
# HTTP proxy to reach the actual OpenVPN
# server, put the proxy server/IP and
# port number here. See the man page
# if your proxy server requires
# authentication.
;http-proxy-retry # retry on connection failures
;http-proxy [proxy server] [proxy port #]
# Wireless networks often produce a lot
# of duplicate packets. Set this flag
# to silence duplicate packet warnings.
;mute-replay-warnings
# SSL/TLS parms.
# See the server config file for more
# description. It's best to use
# a separate .crt/.key file pair
# for each client. A single ca
# file can be used for all clients.
#ca ca.crt
#cert client.crt
#key client.key
# Verify server certificate by checking that the
# certicate has the correct key usage set.
# This is an important precaution to protect against
# a potential attack discussed here:
# http://openvpn.net/howto.html#mitm
#
# To use this feature, you will need to generate
# your server certificates with the keyUsage set to
# digitalSignature, keyEncipherment
# and the extendedKeyUsage to
# serverAuth
# EasyRSA can do this for you.
remote-cert-tls server
# If a tls-auth key is used on the server
# then every client must also have the key.
tls-auth ta.key 1
# Select a cryptographic cipher.
# If the cipher option is used on the server
# then you must also specify it here.
# Note that 2.4 client/server will automatically
# negotiate AES-256-GCM in TLS mode.
# See also the ncp-cipher option in the manpage
cipher AES-128-CBC
auth SHA256
key-direction 1
# Enable compression on the VPN link.
# Don't enable this unless it is also
# enabled in the server config file.
#comp-lzo
# Set log file verbosity.
verb 3
# Silence repeating messages
;mute 20
# script-security 2
# up /etc/openvpn/update-resolv-conf
# down /etc/openvpn/update-resolv-conf
<ca>
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
</ca>
<cert>
Certificate:
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
-----END PRIVATE KEY-----
</key>
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
-----END OpenVPN Static key V1-----
</tls-auth>
When my server boots up I use the command
Code: Select all
sudo iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o ens4 -j MASQUERADE