I went through the this and several other forums and tutorials and I think I am very close to achieve the goal but it seems that there is something (hopefully) small still missing in my configuration. All the data (IPs, FQDNs, etc.) below do not represent actual values in my environment but were replaced with random (yet consistent) values for easy of read.
I can tracert (ICMP) RaspberryPi from my Windows but when I they to SSH to it it is not working at all (not even SYN ACK seen on the WireShark on Windows host). Any help highly appreciated
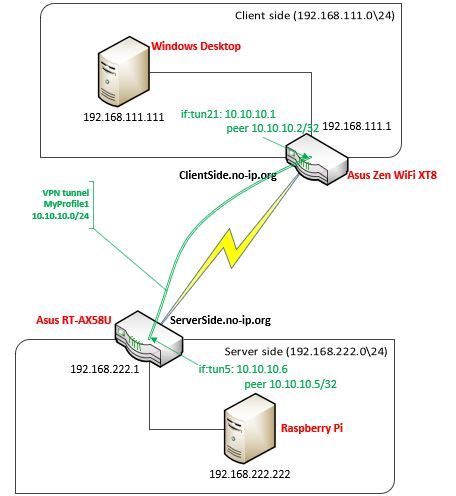
My environment:
Two Asus routers in two different geographical locations.
Client Side:
- Asus Zen WiFi XT8 (stock newest firmware, no tcpdump
 )
) - local network 192.168.111.0/24
- Dynamic Public IP with DynDNS ClientSide.no-ip.org
- Windows Desktop at 192.168.111.111
- Self-signed certificates created on a different host with OpenSSL with CN=ClientSide.no-ip.org and SAN1=ClientSide.no-ip.org and SAN2=router.asus.com
The above SAN2 is to get rid of the warning when browsing to the router from within the LAN
- Asus RT-AX58U (stock newest firmware, no tcpdump
 )
) - local network 192.168.222.0/24
- Dynamic Public IP with DynDNS ServerSide.no-ip.org
- Test Raspebry Pi at 192.168.222.222
- Self-signed certificates created on a different host with OpenSSL with CN=ServereSide.no-ip.org and SAN1=ServerSide.no-ip.org and SAN2=router.asus.com
The above SAN2 is to get rid of the warning when browsing to the router from within the LAN
//Note: I couldn't make the Asus stock firmware to log OpenVPN logs with
and the logs collected by Asus by default are pretty much empty...--verb 4
MyProfile1 in the _etc_openvpn_server1_ccd_MyProfile1
iroute 192.168.111.0 255.255.255.0
Server config in the _etc_openvpn_server1_config.ovpn
# Automatically generated configuration
# Tunnel options
proto tcp4-server
port 1194
dev tun21
sndbuf 0
rcvbuf 0
keepalive 10 30
up '/etc/openvpn/ovpn-up'
down '/etc/openvpn/ovpn-down'
setenv ovpn_type 0
setenv unit 1
script-security 2
daemon vpnserver1
verb 3
status-version 2
status status 10
comp-lzo adaptive
plugin /usr/lib/openvpn-plugin-auth-pam.so openvpn
# Server Mode
server 10.10.10.0 255.255.255.0
client-config-dir ccd
client-to-client
ccd-exclusive
route 192.168.111.0 255.255.255.0
push "route 192.168.111.0 255.255.255.0"
push "route 192.168.222.0 255.255.255.0 vpn_gateway 500"
verify-client-cert none
username-as-common-name
# Data Channel Encryption Options
auth SHA256
cipher AES-256-CBC
# TLS Mode Options
ca ca.crt
dh dh.pem
cert server.crt
key server.key
# Custom Configuration
route 192.168.111.0 255.255.255.0
Client config taken from the server in the _etc_openvpn_server1_client.ovpn
remote ServerSide.no-ip.org 1194
float
nobind
proto tcp-client
dev tun
sndbuf 0
rcvbuf 0
keepalive 10 30
comp-lzo adaptive
auth-user-pass
client
auth SHA256
cipher AES-256-CBC
remote-cert-tls server
<ca>
-----BEGIN CERTIFICATE-----
SANITIZED
-----END CERTIFICATE-----
</ca>
// Note: using code below as it has const width fonts
tracert from Windows host
Code: Select all
C:\Users\USER1\tracert 192.168.222.222
Tracing route to 192.168.222.222
over a maximum of 30 hops:
1 3 ms 3 ms 2 ms 192.168.111.1
2 75 ms 47 ms 69 ms 10.10.10.1
3 60 ms 50 ms 50 ms 192.168.222.222
Trace complete.
Code: Select all
user1@ServerSide:/tmp/etc/openvpn/server1# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default ISP 0.0.0.0 UG 0 0 0 eth4
10.10.10.0 10.10.10.2 255.255.255.0 UG 0 0 0 tun21
10.10.10.2 * 255.255.255.255 UH 0 0 0 tun21
punlic IP0 ISP 255.255.255.255 UGH 1 0 0 eth4
public IP1 ISP 255.255.255.255 UGH 1 0 0 eth4
public IP2 * 255.255.254.0 U 0 0 0 eth4
public IP3 * 255.255.255.255 UH 0 0 0 eth4
127.0.0.0 * 255.0.0.0 U 0 0 0 lo
192.168.111.0 10.10.10.2 255.255.255.0 UG 0 0 0 tun21
192.168.222.0 * 255.255.255.0 U 0 0 0 br0
239.0.0.0 * 255.0.0.0 U 0 0 0 br0
Code: Select all
user1@ClientSide:/tmp/etc/openvpn/client5# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default ISP1 0.0.0.0 UG 0 0 0 eth0
10.10.10.0 10.10.10.5 255.255.255.0 UG 0 0 0 tun15
10.10.10.5 * 255.255.255.255 UH 0 0 0 tun15
Public IP4 ISP2 255.255.255.255 UGH 1 0 0 eth0
Public IP4 ISP2 255.255.255.255 UGH 1 0 0 eth0
Public IP5 * 255.255.255.0 U 0 0 0 eth0
Public IP6 * 255.255.255.255 UH 0 0 0 eth0
127.0.0.0 * 255.0.0.0 U 0 0 0 lo
192.168.111.0 * 255.255.255.0 U 0 0 0 br0
192.168.222.0 10.10.10.5 255.255.255.0 UG 0 0 0 tun15
Code: Select all
user1@ServerSide:/tmp/etc/openvpn/server1#iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
11 2039 ACCEPT all -- tun21 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:1194
9 602 INPUT_PING icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
17458 5193K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
14 636 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 state INVALID
35729 12M PTCSRVWAN all -- !br0 * 0.0.0.0/0 0.0.0.0/0
726 48016 PTCSRVLAN all -- br0 * 0.0.0.0/0 0.0.0.0/0
0 0 DROP tcp -- !lo * 0.0.0.0/0 0.0.0.0/0 tcp dpt:5152
726 48016 ACCEPT all -- br0 * 0.0.0.0/0 0.0.0.0/0 state NEW
28027 9810K ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 state NEW
4440 1772K ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:67 dpt:68
1332 69312 ACCEPT tcp -- * * 0.0.0.0/0 192.168.222.1 ctstate DNAT tcp dpt:8443
27 1316 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
0 0 INPUT_ICMP icmp -- * * 0.0.0.0/0 0.0.0.0/0
1903 83232 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
48 2616 ACCEPT all -- tun21 * 0.0.0.0/0 0.0.0.0/0
50 5450 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 DROP all -- !br0 eth4 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- br0 br0 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 state INVALID
4 240 ACCEPT all -- br0 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate DNAT
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 56533 packets, 20M bytes)
pkts bytes target prot opt in out source destination
896 55622 OUTPUT_DNS udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 u32 "0x0>>0x16&0x3c@0x8>>0xf&0x1=0x0"
0 0 OUTPUT_DNS tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:53 u32 "0x0>>0x16&0x3c@0xc>>0x1a&0x3c@0x8>>0xf&0x1=0x0"
56533 20M OUTPUT_IP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ACCESS_RESTRICTION (0 references)
pkts bytes target prot opt in out source destination
Chain DNSFILTER_DOT (0 references)
pkts bytes target prot opt in out source destination
Chain FUPNP (0 references)
pkts bytes target prot opt in out source destination
Chain IControls (0 references)
pkts bytes target prot opt in out source destination
Chain INPUT_ICMP (1 references)
pkts bytes target prot opt in out source destination
0 0 RETURN icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
0 0 RETURN icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 13
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain INPUT_PING (1 references)
pkts bytes target prot opt in out source destination
9 602 DROP icmp -- eth4 * 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT_DNS (2 references)
pkts bytes target prot opt in out source destination
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
Chain OUTPUT_IP (1 references)
pkts bytes target prot opt in out source destination
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED/24
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED
Chain PControls (0 references)
pkts bytes target prot opt in out source destination
Chain PTCSRVLAN (1 references)
pkts bytes target prot opt in out source destination
Chain PTCSRVWAN (1 references)
pkts bytes target prot opt in out source destination
Chain SECURITY (0 references)
pkts bytes target prot opt in out source destination
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcpflags: 0x17/0x02 limit: avg 1/sec burst 5
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcpflags: 0x17/0x02
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcpflags: 0x17/0x04 limit: avg 1/sec burst 5
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcpflags: 0x17/0x04
0 0 RETURN icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8 limit: avg 1/sec burst 5
0 0 DROP icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
0 0 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
Chain WGNPControls (0 references)
pkts bytes target prot opt in out source destination
Chain default_block (0 references)
pkts bytes target prot opt in out source destination
Chain logaccept (0 references)
pkts bytes target prot opt in out source destination
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 state NEW LOG flags 7 level 4 prefix "ACCEPT "
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0
Chain logdrop (0 references)
pkts bytes target prot opt in out source destination
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 state NEW LOG flags 7 level 4 prefix "DROP "
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain logdrop_dns (16 references)
pkts bytes target prot opt in out source destination
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 LOG flags 7 level 4 prefix "DROP_DNS "
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain logdrop_ip (6 references)
pkts bytes target prot opt in out source destination
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 LOG flags 7 level 4 prefix "DROP_IP "
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Code: Select all
user1@ClientSide:/tmp/etc/openvpn/client5# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
12 710 ACCEPT all -- tun15 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- tap15 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- tap15 * 0.0.0.0/0 0.0.0.0/0
2835 235K INPUT_PING icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
287K 60M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2446 114K DROP all -- * * 0.0.0.0/0 0.0.0.0/0 state INVALID
342K 81M PTCSRVWAN all -- !br0 * 0.0.0.0/0 0.0.0.0/0
202K 23M PTCSRVLAN all -- br0 * 0.0.0.0/0 0.0.0.0/0
1 40 DROP tcp -- !lo * 0.0.0.0/0 0.0.0.0/0 tcp dpt:5152
202K 23M ACCEPT all -- br0 * 0.0.0.0/0 0.0.0.0/0 state NEW
335K 80M ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 state NEW
0 0 ACCEPT 2 -- * * 0.0.0.0/0 224.0.0.0/4
0 0 ACCEPT udp -- * * 0.0.0.0/0 224.0.0.0/4 udp dpt:!1900
126 41545 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:67 dpt:68
333 18324 ACCEPT tcp -- * * 0.0.0.0/0 192.168.111.1 ctstate DNAT tcp dpt:8443
0 0 INPUT_ICMP icmp -- * * 0.0.0.0/0 0.0.0.0/0
5923 340K DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
182 12940 ACCEPT all -- tun15 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- tap15 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- tap15 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT udp -- * * 0.0.0.0/0 224.0.0.0/4
412K 102M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 DROP all -- !br0 eth0 0.0.0.0/0 0.0.0.0/0
1 28 ACCEPT all -- br0 br0 0.0.0.0/0 0.0.0.0/0
7391 402K DROP all -- * * 0.0.0.0/0 0.0.0.0/0 state INVALID
64393 22M ACCEPT all -- br0 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate DNAT
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 684K packets, 141M bytes)
pkts bytes target prot opt in out source destination
47663 3242K OUTPUT_DNS udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 u32 "0x0>>0x16&0x3c@0x8>>0xf&0x1=0x0"
3 258 OUTPUT_DNS tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:53 u32 "0x0>>0x16&0x3c@0xc>>0x1a&0x3c@0x8>>0xf&0x1=0x0"
801K 197M OUTPUT_IP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ACCESS_RESTRICTION (0 references)
pkts bytes target prot opt in out source destination
Chain DNSFILTER_DOT (0 references)
pkts bytes target prot opt in out source destination
Chain FUPNP (0 references)
pkts bytes target prot opt in out source destination
Chain IControls (0 references)
pkts bytes target prot opt in out source destination
Chain INPUT_ICMP (1 references)
pkts bytes target prot opt in out source destination
0 0 RETURN icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
0 0 RETURN icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 13
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain INPUT_PING (1 references)
pkts bytes target prot opt in out source destination
75 2926 DROP icmp -- eth0 * 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT_DNS (2 references)
pkts bytes target prot opt in out source destination
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
0 0 logdrop_dns all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "|SANITIZED|" ALGO name bm TO 65535 ICASE
Chain OUTPUT_IP (1 references)
pkts bytes target prot opt in out source destination
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED/24
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED
0 0 logdrop_ip all -- * * 0.0.0.0/0 SANITIZED
Chain PControls (0 references)
pkts bytes target prot opt in out source destination
Chain PTCSRVLAN (1 references)
pkts bytes target prot opt in out source destination
Chain PTCSRVWAN (1 references)
pkts bytes target prot opt in out source destination
Chain SECURITY (0 references)
pkts bytes target prot opt in out source destination
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcpflags: 0x17/0x02 limit: avg 1/sec burst 5
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcpflags: 0x17/0x02
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcpflags: 0x17/0x04 limit: avg 1/sec burst 5
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcpflags: 0x17/0x04
0 0 RETURN icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8 limit: avg 1/sec burst 5
0 0 DROP icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
0 0 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
Chain VL (0 references)
pkts bytes target prot opt in out source destination
Chain WGNPControls (0 references)
pkts bytes target prot opt in out source destination
Chain default_block (0 references)
pkts bytes target prot opt in out source destination
Chain logaccept (0 references)
pkts bytes target prot opt in out source destination
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 state NEW LOG flags 7 level 4 prefix "ACCEPT "
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0
Chain logdrop (0 references)
pkts bytes target prot opt in out source destination
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 state NEW LOG flags 7 level 4 prefix "DROP "
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain logdrop_dns (16 references)
pkts bytes target prot opt in out source destination
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 LOG flags 7 level 4 prefix "DROP_DNS "
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain logdrop_ip (6 references)
pkts bytes target prot opt in out source destination
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 LOG flags 7 level 4 prefix "DROP_IP "
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
