A strange case in Mikrotik OpenVPN client mode
Posted: Thu Jul 13, 2023 6:45 am
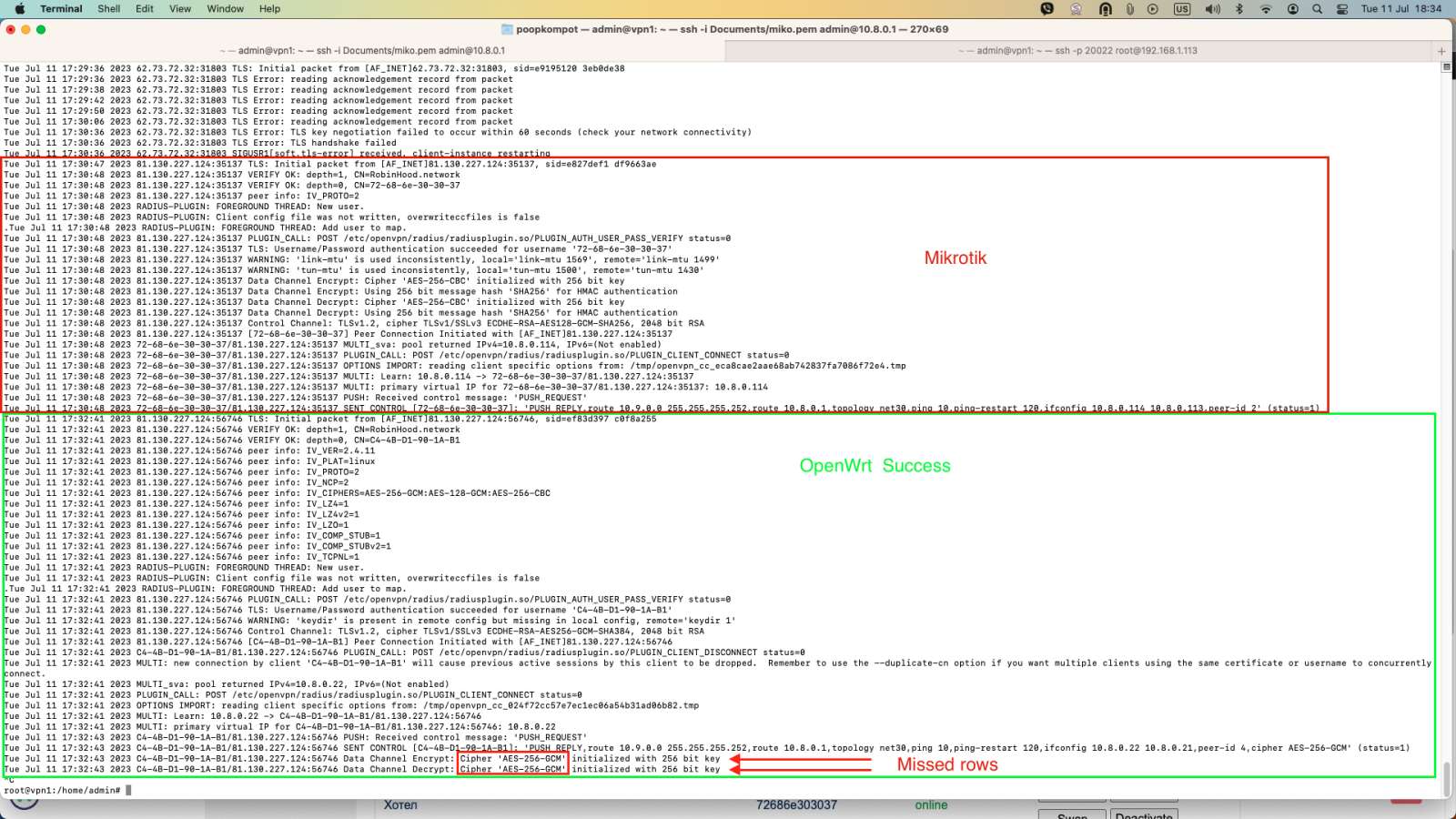
I have on Debian GNU/Linux 9.13 (stretch) in AWS, OpenVPN 2.4.0 x86_64-pc-linux-gnu. A dozen OpenWrt clients are connected to it, and everything is working perfectly. I configure and connect a device with RouterOS 7.10.1 Everything seems fine, but when I try to check the connection with ping - there is none.
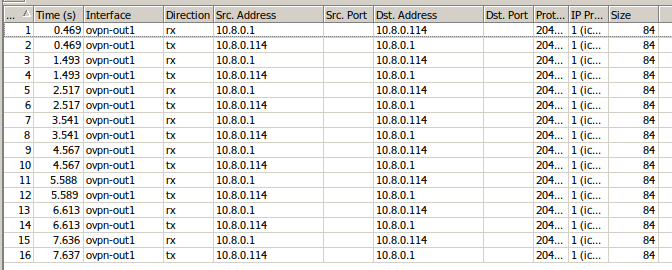
The strange thing is that everything seems correctly configured and when I ping from the server to the client in the client interface sniffer I see traffic from and to the server.
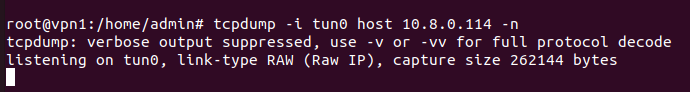
When I ping from the client side to the server on the tun interface on the server side no traffic is received from the client
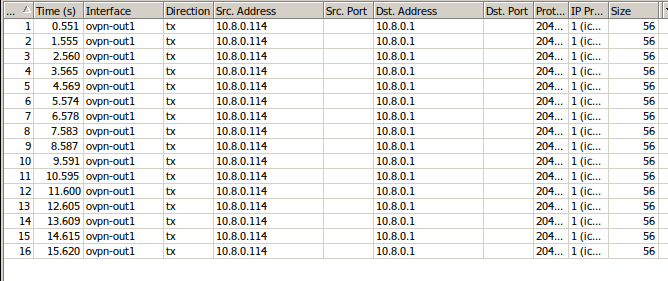
but I see outgoing traffic in the client interface
Now in summary I will share my configuration:
Server-side
server.conf
Client-side
config
Any help would be greatly appreciated by me.
Nikolay Petrov
P.S. No issues with AWS firewall. Still, there are working clients with OpenWrt!

The strange thing is that everything seems correctly configured and when I ping from the server to the client in the client interface sniffer I see traffic from and to the server.

When I ping from the client side to the server on the tun interface on the server side no traffic is received from the client

but I see outgoing traffic in the client interface

Now in summary I will share my configuration:
Server-side
server.conf
server routesport 1194
proto udp
dev tun
ca /etc/openvpn/ca.crt
cert /etc/openvpn/server.crt
key /etc/openvpn/server.key # This file should be kept secret
dh /etc/openvpn/dh.pem
server 10.8.0.0 255.255.240.0
ifconfig-pool-persist ipp.txt
push "route 10.9.0.0 255.255.255.252"
client-config-dir /etc/openvpn/ccd/
route 10.9.0.0 255.255.255.252
keepalive 10 120
cipher AES-256-CBC
auth SHA256
user nobody
group nogroup
persist-key
persist-tun
plugin /etc/openvpn/radius/radiusplugin.so /etc/openvpn/radius/radius.cnf
status openvpn-status.log
log openvpn.log
verb 3
management localhost 7505
tun-mtu 1500
mssfix 1430
server firewallroot@vpn1:/home/admin# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default ip-172-31-0-1.e 0.0.0.0 UG 0 0 0 eth0
10.8.0.0 ip-10-8-0-2.eu- 255.255.240.0 UG 0 0 0 tun0
ip-10-8-0-2.eu- 0.0.0.0 255.255.255.255 UH 0 0 0 tun0
10.9.0.0 ip-10-8-0-2.eu- 255.255.255.252 UG 0 0 0 tun0
172.31.0.0 0.0.0.0 255.255.240.0 U 0 0 0 eth0
root@vpn1:/home/admin# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Client-side
config
routes[admin@MikroTik] > interface/ovpn-client/print
Flags: X - disabled; R - running; H - hw-crypto
0 R name="ovpn-out1" mac-address=02:3F:1F:C9:AB:B0 max-mtu=1500
connect-to=vpn1.xxx.com port=1194 mode=ip protocol=udp
user="XX-XX-XX-XX-XX-XX" password="XXXXXXXXXXX" profile=default
certificate=client.crt_0 verify-server-certificate=no tls-version=any
auth=sha256 cipher=aes256-cbc use-peer-dns=yes add-default-route=no
route-nopull=no disconnect-notify=yes
[admin@MikroTik] >
firewall[admin@MikroTik] > ip/route/print
Flags: D - DYNAMIC; A - ACTIVE; c, d, v, y - BGP-MPLS-VPN
Columns: DST-ADDRESS, GATEWAY, DISTANCE
DST-ADDRESS GATEWAY DISTANCE
DAd 0.0.0.0/0 192.168.1.254 1
DAv 10.8.0.1/32 10.8.0.113 1
DAc 10.8.0.113/32 ovpn-out1 0
DAv 10.9.0.0/30 10.8.0.113 1
DAc 192.168.1.0/24 ether1 0
[admin@MikroTik] >
The only disturbing thing is in the server logs:[admin@MikroTik] /ip/firewall> filter/print
Flags: X - disabled, I - invalid; D - dynamic
0 D ;;; special dummy rule to show fasttrack counters
chain=forward action=passthrough
[admin@MikroTik] /ip/firewall>

Any help would be greatly appreciated by me.
Nikolay Petrov
P.S. No issues with AWS firewall. Still, there are working clients with OpenWrt!