I've set up my OpenVPN on my DD-WRT Asus router. My OpenVPN network is 10.1.1.0 / 255.255.255.0 ( tun2 ). I can connect to my VPN Server remotely by tethering my laptop to my mobile phone ( On my Wireless Provider's Network ) then connecting over to my external ISP IP on which my OpenVPN server is residing on. I see the CCD files get applied to my User, as they should, restricting me to a specific VLAN ( 10.30.0.X ). My CCD config is:
CCD File:
Code: Select all
push "route 10.30.0.0 255.255.255.0"Connecting to devices on 10.30.0.X, works fine, which is expected. But I can also connect to devices on my local network which is on 192.168.0.X . I should not be able too. When I check where I logged in from on the target machine, the IP listed is 192.168.0.100, which is the OpenVPN Server local IP, NOT my VPN IP 10.1.1.2 . Because of this, restricting traffic via F/W rules doesn't work against 10.1.1.0/24 .
Appears when I initiate an SSH connection from my laptop to a local machine on 192.168.0.X, for example, the OpenVPN server forwards those packets from tun2 over to br0 from which it then initiates a connection to the target machine. Since the connection appears to be routed through br0, which is on 192.168.0.100, the connection to other machines on the local subnet of course works.
This Asus router is also running OSPF for automatic routing. ( This is a routing protocol that establishes routes automatically. )
Including a visual of the setup.
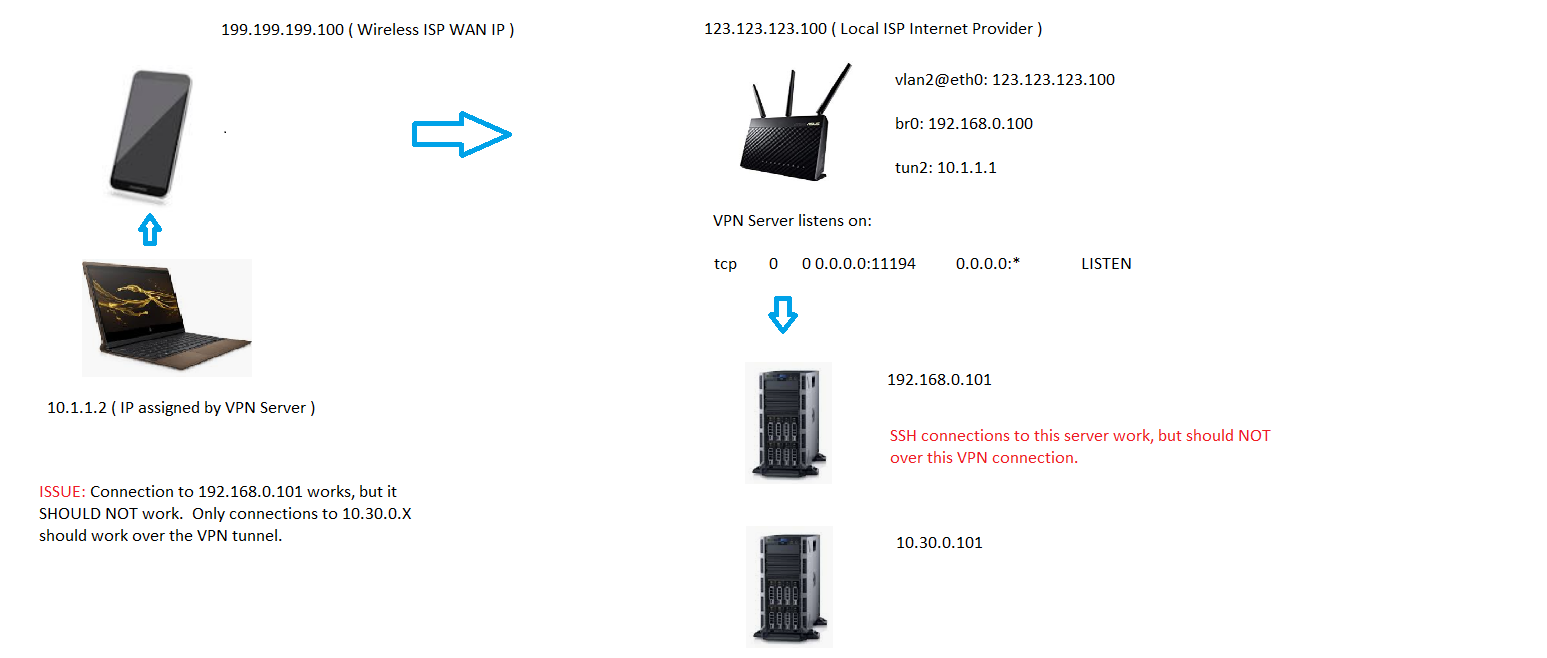
How do I prevent this and restrict connections for the said client only to 10.30.0.X as per the CCD file definition?
Regards,
OpenVPN Server
dh /openvpn/dh.pem
ca /openvpn/ca.crt
cert /openvpn/cert.pem
key /openvpn/key.pem
tls-auth /openvpn/ta.key 0
keepalive 10 120
verb 3
mute 3
syslog
writepid /var/run/openvpnd.pid
management 127.0.0.1 14
management-log-cache 100
topology subnet
script-security 2
port 11194
proto tcp4-server
cipher aes-256-cbc
auth sha256
client-connect /openvpn/clcon.sh
client-disconnect /openvpn/cldiscon.sh
client-config-dir /openvpn/ccd
comp-lzo adaptive
tls-server
ifconfig-pool-persist /openvpn/ip-pool 86400
client-to-client
push "redirect-gateway def1"
tls-cipher TLS-DHE-RSA-WITH-AES-256-CBC-SHA256
tcp-nodelay
tun-mtu 1500
mtu-disc yes
server 10.1.1.0 255.255.255.0
dev tun2
auth-nocache
OpenVPN Client
client
dev tun2
proto tcp
remote access.mysite.com 11194
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert UserGuest.crt
key UserGuest.key
remote-cert-tls server
tls-auth ta.key 1
cipher AES-256-CBC
auth SHA256
comp-lzo
verb 3
auth-nocache
CCD:
Code: Select all
push "route 10.30.0.0 255.255.255.0"F/W:
Code: Select all
# ----------------------
# VPN Specific
# ----------------------
# Allow remote connections to the OpenVPN server.
iptables -A INPUT -p tcp --dport 11194-d 123.123.123.100 -j ACCEPT
iptables -A INPUT -p udp --dport 11194 -d 123.123.123.100 -j ACCEPT
# For Web Traffic to the VLAN's.
iptables -t nat -A POSTROUTING -s 10.1.1.0/24 -j MASQUERADE
# This has no apparent effect.
iptables -A INPUT -s 10.1.1.0/24 -j REJECT --reject-with icmp-port-unreachable
iptables -A OUTPUT -s 10.1.1.0/24 -j REJECT --reject-with icmp-port-unreachable