am trying to configure openvpn with ldap or pam authentication with my active directory server (openvpn server and Activedirectory server are in the same network).
i tryied with ldap and i can't succes login so i decide to test PAM but i have same issue
Below all of my conf and log file:
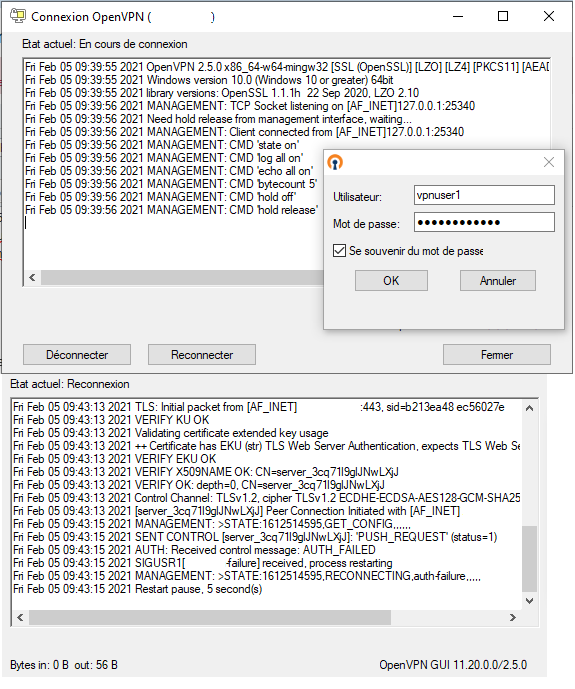
log file when tryin to connect with openvpn GUI using vpn profile
Code: Select all
Thu Feb 04 13:49:49 2021 OpenVPN 2.4.7 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 25 2019
Thu Feb 04 13:49:49 2021 Windows version 6.2 (Windows 8 or greater) 64bit
Thu Feb 04 13:49:49 2021 library versions: OpenSSL 1.1.0j 20 Nov 2018, LZO 2.10
Enter Management Password:
Thu Feb 04 13:49:49 2021 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25361
Thu Feb 04 13:49:49 2021 Need hold release from management interface, waiting...
Thu Feb 04 13:49:50 2021 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25361
Thu Feb 04 13:49:50 2021 MANAGEMENT: CMD 'state on'
Thu Feb 04 13:49:50 2021 MANAGEMENT: CMD 'log all on'
Thu Feb 04 13:49:50 2021 MANAGEMENT: CMD 'echo all on'
Thu Feb 04 13:49:50 2021 MANAGEMENT: CMD 'bytecount 5'
Thu Feb 04 13:49:50 2021 MANAGEMENT: CMD 'hold off'
Thu Feb 04 13:49:50 2021 MANAGEMENT: CMD 'hold release'
Thu Feb 04 13:49:51 2021 MANAGEMENT: CMD 'username "Auth" "soo"'
Thu Feb 04 13:49:51 2021 MANAGEMENT: CMD 'password [...]'
Thu Feb 04 13:49:51 2021 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Thu Feb 04 13:49:51 2021 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Thu Feb 04 13:49:51 2021 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Thu Feb 04 13:49:51 2021 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Thu Feb 04 13:49:51 2021 TCP/UDP: Preserving recently used remote address: [AF_INET]x.x.x.x:443
Thu Feb 04 13:49:51 2021 Socket Buffers: R=[65536->65536] S=[65536->65536]
Thu Feb 04 13:49:51 2021 Attempting to establish TCP connection with [AF_INET]x.x.x.x:443 [nonblock]
Thu Feb 04 13:49:51 2021 MANAGEMENT: >STATE:1612442991,TCP_CONNECT,,,,,,
Thu Feb 04 13:49:52 2021 TCP connection established with [AF_INET]x.x.x.x:443
Thu Feb 04 13:49:52 2021 TCP_CLIENT link local: (not bound)
Thu Feb 04 13:49:52 2021 TCP_CLIENT link remote: [AF_INET]x.x.x.x:443
Thu Feb 04 13:49:52 2021 MANAGEMENT: >STATE:1612442992,WAIT,,,,,,
Thu Feb 04 13:49:52 2021 MANAGEMENT: >STATE:1612442992,AUTH,,,,,,
Thu Feb 04 13:49:52 2021 TLS: Initial packet from [AF_INET]x.x.x.x:443, sid=7e9e0c1d 2ff063b6
Thu Feb 04 13:49:53 2021 VERIFY OK: depth=1, CN=cn_ft8Ph0hTjechqqQz
Thu Feb 04 13:49:53 2021 VERIFY KU OK
Thu Feb 04 13:49:53 2021 Validating certificate extended key usage
Thu Feb 04 13:49:53 2021 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Thu Feb 04 13:49:53 2021 VERIFY EKU OK
Thu Feb 04 13:49:53 2021 VERIFY X509NAME OK: CN=server_3cq71l9glJNwLXjJ
Thu Feb 04 13:49:53 2021 VERIFY OK: depth=0, CN=server_3cq71l9glJNwLXjJ
Thu Feb 04 13:49:53 2021 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit EC, curve: prime256v1
Thu Feb 04 13:49:53 2021 [server_3cq71l9glJNwLXjJ] Peer Connection Initiated with [AF_INET]x.x.x.x:443
Thu Feb 04 13:49:54 2021 MANAGEMENT: >STATE:1612442994,GET_CONFIG,,,,,,
Thu Feb 04 13:49:54 2021 SENT CONTROL [server_3cq71l9glJNwLXjJ]: 'PUSH_REQUEST' (status=1)
Thu Feb 04 13:49:54 2021 AUTH: Received control message: AUTH_FAILED
Thu Feb 04 13:49:54 2021 SIGUSR1[soft,auth-failure] received, process restarting
Thu Feb 04 13:49:54 2021 MANAGEMENT: >STATE:1612442994,RECONNECTING,auth-failure,,,,,
Thu Feb 04 13:49:54 2021 Restart pause, 5 second(s)
Thu Feb 04 13:50:02 2021 MANAGEMENT: Client disconnected
Thu Feb 04 13:50:02 2021 ERROR: could not read Auth username/password/ok/string from management interface
Thu Feb 04 13:50:02 2021 Exiting due to fatal error
proto tcp
dev tun
user nobody
group nobody
persist-key
persist-tun
keepalive 10 120
topology subnet
server 10.8.8.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 1.1.1.1"
push "redirect-gateway def1 bypass-dhcp"
dh none
ecdh-curve prime256v1
tls-crypt tls-crypt.key
crl-verify crl.pem
ca ca.crt
cert server_3cq71l9glJNwLXjJ.crt
key server_3cq71l9glJNwLXjJ.key
auth SHA256
cipher AES-128-GCM
ncp-ciphers AES-128-GCM
pull-filter ignore "auth token"
tls-server
tls-version-min 1.2
tls-cipher TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256
client-config-dir /etc/openvpn/ccd
status /var/log/openvpn/status.log
verb 3
client-cert-not-required
script-security 2
#auth-user-pass-verify ldap-check-user.sh via-env
username-as-common-name
#plugin /usr/lib64/openvpn/plugin/lib/openvpn-auth-ldap.so /etc/openvpn/auth/auth-ldap.conf
#plugin /usr/lib64/openvpn/plugin/lib/openvpn-auth-ldap.so auth-ldap.conf
plugin /usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so /etc/pam.d/openvpn
/etc/nslcd.conf
Code: Select all
uid nslcd
gid ldap
uri ldap://ActiveDirectory-IP/
base dc=mydomain,dc=local
binddn cn=testopenvpn,dc=OPENVPNAD,dc=local
bindpw password
scope sub
base group ou=Users,dc=mydomain,dc=local
base passwd ou=Users,dc=mydomain,dc=local
base shadow ou=Users,dc=mydomain,dc=local
bind_timelimit 30
timelimit 30
pagesize 1000
referrals off
filter passwd (&(objectClass=user)(memberOf=cn=vpnusers,ou=Users,dc=mydomain,dc=local)
map passwd uid sAMAccountName
filter shadow (&(objectClass=user)(memberOf=cn=vpnusers,ou=Users,dc=mydomain,dc=local)
map shadow uid sAMAccountName
tls_reqcert never/etc/pam.d/openvpn
Code: Select all
#auth sufficient pam_ldap.so minimum_uid=1000 use_first_pass
#auth required pam_deny.so
#password sufficient pam_ldap.so minimum_uid=1000 use_first_pass
#password required pam_deny.so
auth required pam_ldap.so
account sufficient pam_permit.so
session required pam_permit.soCode: Select all
<LDAP>
#URL ldap://mydomain.local
URL ldap://ActiveDirectory-ip:389
BindDN "CN=testopenvpn,CN=Users,DC=mydomain,DC=local"
Password password
Timeout 15
TLSEnable no
# Follow LDAP Referrals (anonymously)
FollowReferrals no
# TLS CA Certificate File
TLSCACertFile /etc/openvpn/openvpn-ca.crt
</LDAP>
<Authorization>
BaseDN "dc=mydomain,dc=local"
SearchFilter "(&(sAMAccountName=%u)(memberOf=CN=vpnusers,CN=Users,DC=mydomain,DC=local))"
RequireGroup false
</Authorization>profile.ovpn
client
proto tcp-client
remote x.x.x.x 443
dev tun
resolv-retry infinite
nobind
persist-key
persist-tun
auth-user-pass
remote-cert-tls server
verify-x509-name server_3cq71l9glJNwLXjJ name
auth SHA256
auth-nocache
pull-filter ignore "auth token"
cipher AES-128-GCM
tls-client
tls-version-min 1.2
tls-cipher TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256
ignore-unknown-option block-outside-dns
#setenv opt block-outside-dns # Prevent Windows 10 DNS leak
verb 3
Any idea to solve this issue?
Thank you so much in advance.