Page 1 of 1
Cipher AES-256-GCM not available on OpenVPN Access Server, it is normal ?
Posted: Sun Apr 11, 2021 7:59 am
by Elrick91
Hi to all,
I'm currently using OpenVPN Server on Docker. through Synology NAS Server.
I would like to use AES-256-GCM instead of AES-256-CBC.
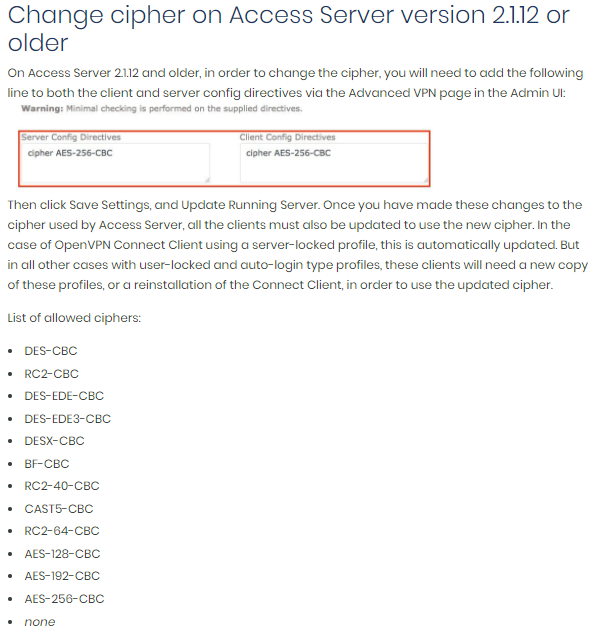
I'm looking on information related on OpenVPN documentation to change cipher on Access Server
but i discover that this encryption is not in the list,
is it normal?
 Is AES-256-GCM supported by OpenVPN Access Server?
Is AES-256-GCM supported by OpenVPN Access Server?
How can I add it to be supported please?
Thank you.
Re: Cipher AES-256-GCM not available on OpenVPN Access Server, it is normal ?
Posted: Mon Apr 12, 2021 4:01 pm
by chilinux
You are referencing a knowledgebase article that is very old at this point.
The current version of OpenVPN AS is 2.8.7 and that article is talking about versions previous to 2.2.
Try running this to see which ciphers are available to you:
/usr/local/openvpn_as/sbin/openvpn-openssl --show-ciphers
I am able to see AES-256-GCM as an option available to me.
You should also be able to see in the logs what cipher is used for the session after the initial handshake.
Re: Cipher AES-256-GCM not available on OpenVPN Access Server, it is normal ?
Posted: Tue Apr 13, 2021 6:13 am
by openvpn_inc
Hello Elrick91,
chilinux is right that you are referencing old documentation from this page:
https://openvpn.net/vpn-server-resource ... ss-server/ - it clearly states in the header that this is for 2.1.12 or older.
There is information on how to select a cipher on newer Access Server versions:
https://openvpn.net/vpn-server-resource ... and_client
However, we recommend leaving it at the defaults if your goal is AES-256-GCM. The default is set to AES-256-CBC but allows an OpenVPN client that is capable of renegotiating the connection to something more efficient - AES-256-GCM. This will happen automatically if the client is capable of doing this.
The reason for an 'old' set of ciphers to exist next to newer ciphers is backward compatibility. Newer OpenVPN version are capable of indicating which ciphers they support and prefer, and can figure it out. However, older clients MUST know the exact cipher being expected by the server, or the connection will simply fail. Older clients did not support AES-256-GCM yet. If you were to configure AES-256-GCM specifically, then older clients would simply not be able to connect. The list you've shown in the screenshot is basically for compatibility. We tell clients and server to use AES-256-CBC, but we also allow better ciphers automatically if the server and client can support it. GCM is better in performance than CBC + signing.
In simple terms, AES-256-CBC is encryption, and on top of that, signing is done. This is a 2-step process. This is somewhat less efficient than AES-256-GCM where encryption and signing occurs in 1 step. Both use AES-256 for the encryption.
So, in short, if you want AES-256-GCM, use a somewhat up-to-date Access Server and leave the default settings in place for the ciphers. You can check in the client logs what cipher is used. Here's a sample from OpenVPN Connect v3:
12/04/2021, 23:12:05 PROTOCOL OPTIONS:
cipher: AES-256-GCM
digest: NONE
compress: COMP_STUBv2
peer ID: 0
Kind regards,
Johan
Re: Cipher AES-256-GCM not available on OpenVPN Access Server, it is normal ?
Posted: Tue Apr 13, 2021 11:26 am
by Elrick91
i write cipher -AES-256-GCM on each side into OpenVPN Access Server and it seems to work.
It's not a problem to me to force AES-256-GCM because i'm will have only one or two clients at max.
And these client will used lastest OpenVPN version.
Does AES-256-GCM cipher is the most advanced/secure to hardening OpenVPN ?
Re: Cipher AES-256-GCM not available on OpenVPN Access Server, it is normal ?
Posted: Tue Apr 13, 2021 2:18 pm
by chilinux
If forcing OpenVPN's cipher on both sides to a specific cipher gives you the result you desire, you are free to use that. Just keep in mind that the OpenVPN handshake to negotiate ciphers exists for a good reason. What is considered the best cipher today might be considered depreciated someday in the future. The negotiated cipher is designed to get you the best cipher over the entire lifespan of using the product.
The answer as to if AES-256-GCM is the most advanced/secure to harden OpenVPN will evolve over time. The answer today and the answer a year from now may not be the same.
Before forcing the cipher to a specific setting, you may want to check the logs and see what the negotiated result is coming out to be.

