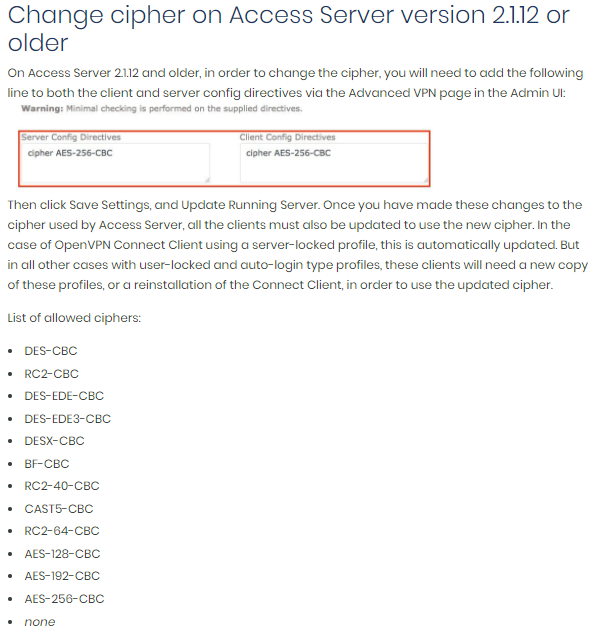
Hello Elrick91,
chilinux is right that you are referencing old documentation from this page:
https://openvpn.net/vpn-server-resource ... ss-server/ - it clearly states in the header that this is for 2.1.12 or older.
There is information on how to select a cipher on newer Access Server versions:
https://openvpn.net/vpn-server-resource ... and_client
However, we recommend leaving it at the defaults if your goal is AES-256-GCM. The default is set to AES-256-CBC but allows an OpenVPN client that is capable of renegotiating the connection to something more efficient - AES-256-GCM. This will happen automatically if the client is capable of doing this.
The reason for an 'old' set of ciphers to exist next to newer ciphers is backward compatibility. Newer OpenVPN version are capable of indicating which ciphers they support and prefer, and can figure it out. However, older clients MUST know the exact cipher being expected by the server, or the connection will simply fail. Older clients did not support AES-256-GCM yet. If you were to configure AES-256-GCM specifically, then older clients would simply not be able to connect. The list you've shown in the screenshot is basically for compatibility. We tell clients and server to use AES-256-CBC, but we also allow better ciphers automatically if the server and client can support it. GCM is better in performance than CBC + signing.
In simple terms, AES-256-CBC is encryption, and on top of that, signing is done. This is a 2-step process. This is somewhat less efficient than AES-256-GCM where encryption and signing occurs in 1 step. Both use AES-256 for the encryption.
So, in short, if you want AES-256-GCM, use a somewhat up-to-date Access Server and leave the default settings in place for the ciphers. You can check in the client logs what cipher is used. Here's a sample from OpenVPN Connect v3:
12/04/2021, 23:12:05 PROTOCOL OPTIONS:
cipher: AES-256-GCM
digest: NONE
compress: COMP_STUBv2
peer ID: 0
Kind regards,
Johan